The MS-ISAC created this flow chart for members and others to follow for identifying and mitigating risk related to this vulnerability:
This graphics is from the MS-ISAC Log4j Vulnerability Response page.
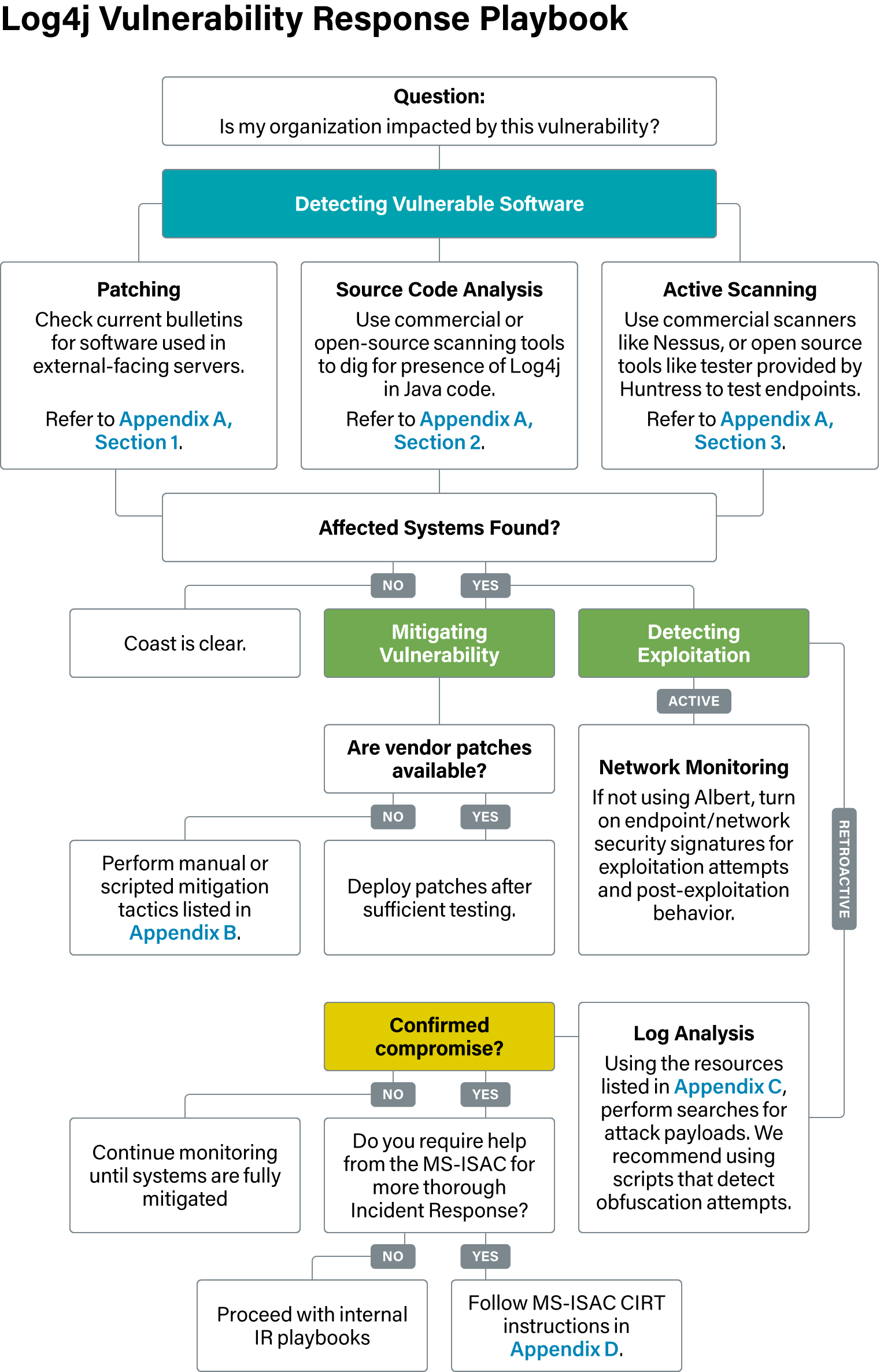
The MS-ISAC created this flow chart for members and others to follow for identifying and mitigating risk related to this vulnerability:
This graphics is from the MS-ISAC Log4j Vulnerability Response page.
